5 Essential Social Media Security Guidelines

We live in the "Internet age" where we spend a considerable amount of time online, therefore, protecting our online identity is non-negotiable. Nobody should be able to have access to sensitive information about us or steal our identity online. Sadly, many have been victims of others having unauthorized access to their social media accounts. Here are five social media guidelines to help you protect your online presence.
A strong password is like a strong lock on the door to your digital world. It's your first line of defense against unauthorized access. Unfortunately, many people don't realize how important this is. In fact, the most common passwords are unbelievably simple. According to a study by cybersecurity firm SplashData, the most commonly used password is still "123456," and "password" itself is a close second.
If your password is this weak, you need to change it immediately.
To create passwords that are strong and difficult to guess, use a mix of upper and lowercase letters, numbers, and symbols. Avoid using information that can be easily guessed like birthdays or names. You can also consider using a trusted password manager if you're in the habit of forgetting your passwords.
Over time, you may have granted various apps access to your social media profiles. It's essential to review these permissions periodically. Revoke access for any apps or services you no longer use or trust. It's crucial to periodically go through the list of connected apps in your social media settings and revoke access for any that you no longer need. This reduces the potential attack surface and minimizes the risk of data breaches.
In addition to these apps, you can also review app permissions manually on both Android and iOS devices.
To do this on Android, go to Settings > Apps > See all apps > [App name] > Permissions. To do this on iOS, go to Settings > Privacy.
Beware of Phishing AttemptsPhishing attacks are a common method cybercriminals use to steal login credentials. Beware of phishing attempts, which often appear as emails or messages from reputable sources, such as social media platforms or well-known brands. These messages may be urgent, compelling you to click a link or provide sensitive information. However, legitimate organizations will not ask for sensitive information through unsolicited messages.
To avoid phishing attacks, always be cautious when clicking on links, especially if the source is unfamiliar. Verify the sender's identity and double-check the URL for any irregularities.
One example of a phishing attempt is the recent Apple event scam. A scammer created a fake YouTube account with the username "Apple Official" and started streaming an older Apple event. The stream included a barcode that led to a page where people were asked to enter sensitive information in exchange for free Bitcoin.
Stay Informed and EducatedCyber threats are always evolving, and it’s important to stay informed as it enables you to adapt to new threats and reinforces your ability to protect your digital assets.
Staying informed is your best bet to staying safe online, you need to be well informed about the latest threats and best practices to avoid the conundrum of having a secure digital identity.
To stay updated, follow reputable security blogs, subscribe to newsletters, and engage with social media pages dedicated to cybersecurity.
5. Enable Two-Factor Authentication (2FA) for Extra Protection
Imagine your online account is a car and your password is the key to the car. If an intruder has your password, they can start the car and drive away. However, 2FA is like a car alarm. Even if the intruder has your key, they cannot drive away without first disarming the alarm.
Two-factor authentication adds an extra layer of security to your social media accounts. It involves having a password and a verification code sent to your phone or authenticator app. By enabling 2FA, you significantly reduce the risk of unauthorized access to your accounts, even if your password is compromised. According to a survey by Google, 2FA can block 99.9% of automated attacks.
Setting up 2FA is relatively simple. Most social media platforms offer this feature in their security settings. Once activated, you'll receive a verification code on your mobile device or authenticator app whenever you log in from an unfamiliar location or device. Without this code, an unauthorized user cannot gain access to your accounts.
Bonus Tip: Use Termii Go for Enhanced Security
Termii Go makes it easy to activate 2FA for your social media accounts as well as apps like Paystack. With Termii Go, you can receive all of your 2FA codes in one place, making it easier to manage and keep them safe. Termii Go also generates a new code every 30 seconds, so you don't have to worry about writing down your codes or forgetting them.
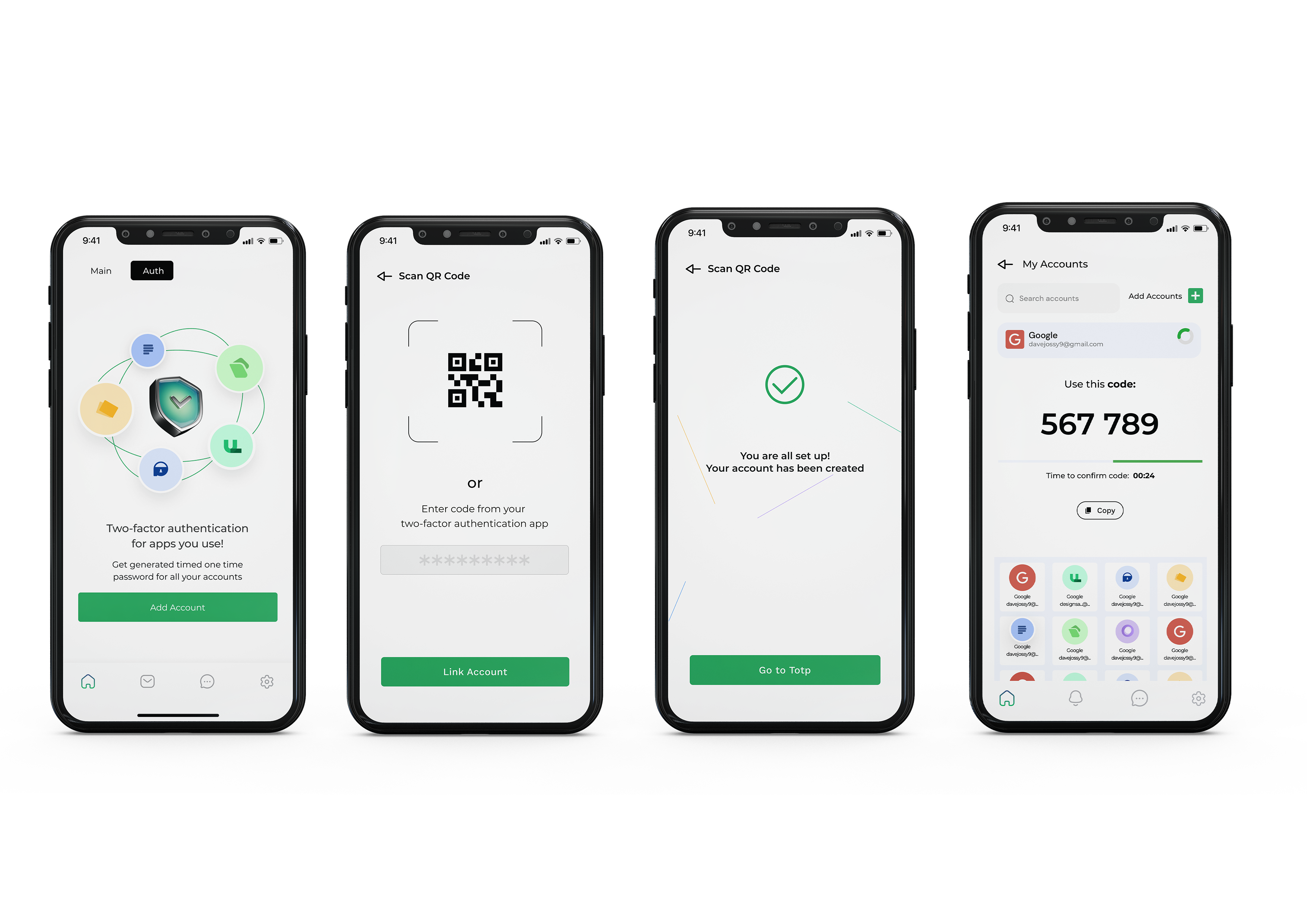
Image source: TermiiGo Mobile App
Check out our guide on how to use Termii Go for secure authentication here.
In conclusion, whether you're a social media enthusiast, a business professional, or a casual user, it's important to protect your online accounts. The digital landscape is full of potential risks, such as phishing attacks and unauthorized access attempts. However, by following these five essential social media security guidelines and using Termii Go to protect your accounts, you can significantly reduce your risk of becoming a victim of cybercrime.
To try Termii Go for free, download from your Appstore and Google playstore.